Security at RoboVault
RoboVault security practices overview for delta neutral yield boosting strategies
At RoboVault as we continue innovating and building out more advanced delta-neutral strategies our main priority will continue being security. Since first launching we have spent a significant amount of time developing a number of processes to ensure our delta neutral can safely and reliably manage users assets.
Vault Infrastructure
For our actual vaults we utilise Yearn’s V2 architecture completely unchanged. We made this decision given Yearn’s track record as leaders in security while utilising this structure allows us to innovate specifically on the strategy side which is where we’ve implemented our automated delta-neutral strategies. Some more info on Yearn’s V2 structure & strategies here.
(note some protocols have overlooked some key security features when developing their own vault infrastructure leading to vulnerabilities. This is why we’ve decided to keep the tried & tested vault infrastructure unchanged allowing us to focus exclusively on our custom delta-neutral strategies within this tried & tested infrastructure)
Rigorous Testing
Throughout the development process we apply quite rigorous testing of our strategies utilising Brownie & its ability to test directly on a fork of a live blockchain. For reference here’s a link to our test suite for our core strategy. Our tests include ensuring all functions work as intended such as harvests, rebalances & withdrawals. While also testing these functions under various conditions such as changes in the LP price for assets utilised within the strategy. Additionally we ensure we test against a number of typical exploits such as price manipulations & sandwich attacks.
Before any strategies are released to the public we also deploy new strategies to private vaults and run them live while monitoring performance & also ensuring all functionality is working as intended.
MEV / Sandwich Protection
As our delta-neutral strategies use LP’s to earn yield in addition to having rebalances complete small swaps between assets to maintain delta-neutral positions. This means without sufficient protection these strategies may be vulnerable to a number of common attacks within DeFi. In order to secure users funds we use a number of different methods to protect against various attacks
Price Manipulation Attacks : By using Yearn’s V2 architecture together with health checks users are unable to significantly alter the vault price per share without taking significant loss
Sandwich Attacks : When completing rebalances to maintain a delta-neutral strategy we swap between assets, in order to protect against sandwich attacks we compare the price of the swapped assets using oracles vs the price of swapped assets to ensure there is no significant difference which would indicate a sandwich attack. Additionally for other key functions such as withdrawals oracle prices are also referenced to protect against external manipulation
Off Chain Infrastructure
Reliable Keepers
Another key component of our delta-neutral strategies is ensuring that the keepers are extremely reliable and can complete rebalances when required. If not, failure of keepers can result in losses to users from high exposure to market movements through IL & also potential liquidations for strategies that contain some borrowing component.
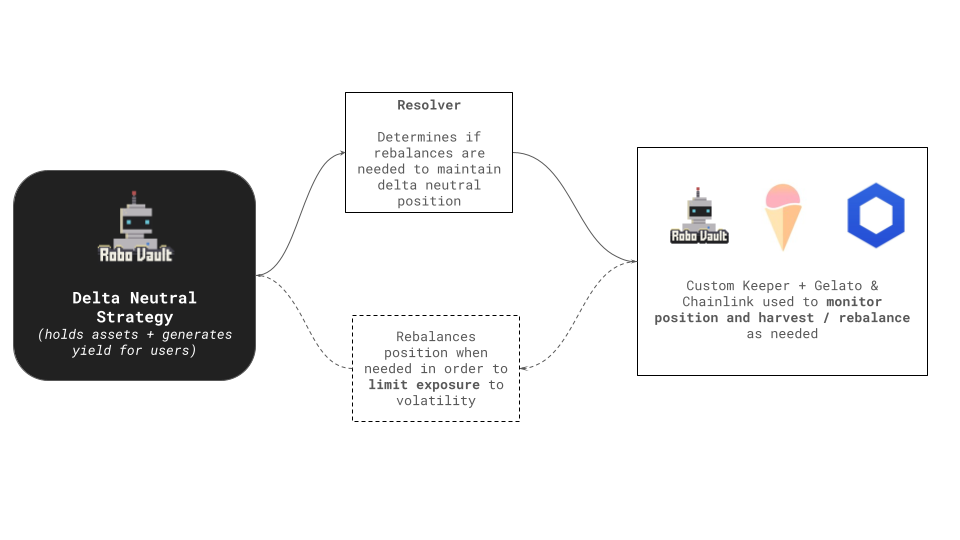
As our delta-neutral strategies require active position management, ensuring we can have 100% confidence in their up-time is crucial for keeping users’ funds secure and not exposing them to large drawdowns. We do this by utilising the best in off-chain automation available leveraging ChainLink Keepers, Gelato Automations in addition to our own custom keepers. Finally to ensure safety on-chain our smart contracts include a number key pieces of logic to ensure none of these keepers can complete malicious attacks. This is primarily done by protecting against sandwich type attacks by comparing LP prices to Oracle prices in addition to limiting the scope of which functions these keepers can actually trigger.
Real Time Monitoring & Alerts
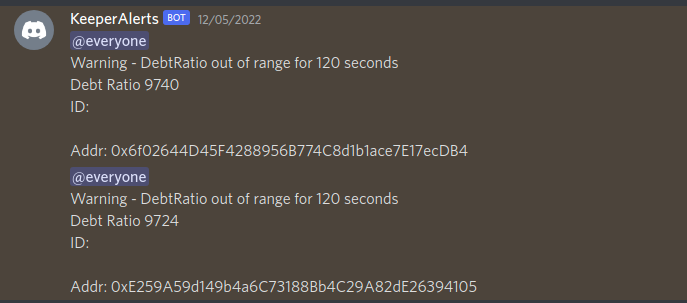
(example of an alert received when automated rebalancing from keepers on 12/05/2022 did not complete as expected)
From our experience operating delta-neutral strategies there are a number of risks that things can go wrong on & off-chain. To mitigate against this risk we’ve built out customised monitoring & alerts for on-chain activity. This allows to track real time on chain data and also receive any real time alerts based on custom rules. Some examples of how this has worked extremely well in the past
- Rebalancing : We actively monitor positions debt ratios to ensure rebalancing is successful, in the past while developing our keeper infrastructure this has been able to provide the team with real time alerts whenever there has been any issues
- Monitoring Oracle Prices : We actively track oracle prices used in any of our delta-neutral strategies against LP prices & CEX prices. Previously on the 26th April 2022 while running our delta-neutral strategies on Fantom we were able to identify an issue where SCREAM’s price oracle was not updating correctly meaning a big price movement could have left the protocol with bad debt. We were able to alert the team to ensure they intervened.
- SCREAM Incident : On the 10th May 2022 SCREAM incurred a significant amount of bad debt due to some adjustments in the protocol. More info here. Our strategies on Fantom actually utilised SCREAM at the time where we had ~$10M of TVL allocated to SCREAM. Due to our active monitoring of protocols we build on top of we were able to rescue these funds before they potentially became locked due to the bad debt incurred by SCREAM.
(Note having reliable off-chain infrastructure to support delta-neutral strategies is extremely hard. Much earlier on in our development cycle in late 2021 we faced some issues & we’ve also seen a number of other protocols face similar issues with their off-chain infrastructure such as Umami & Alpaca)
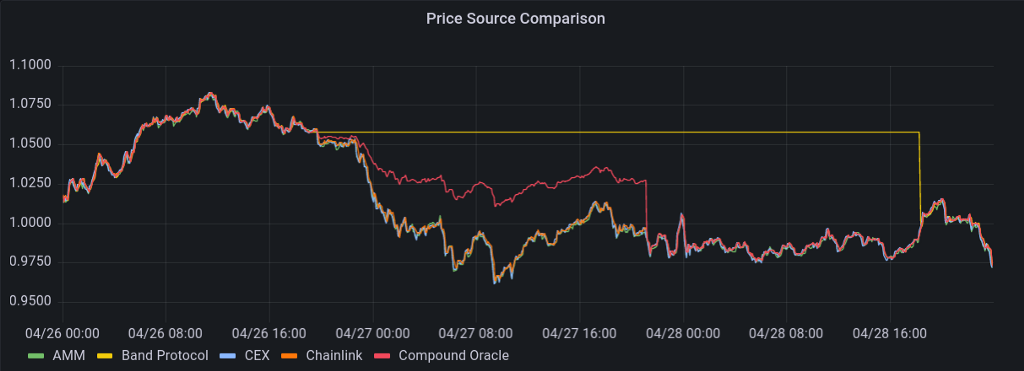
(Data on 26th of April when SCREAMs oracles were not updating correctly due to aggregating from Band, ChainLink where a Band oracle upgrade led to the aggregation no longer pulling the latest values which led to the aggregated Oracle price used by SCREAM being incorrect labelled in the chart as Compound Oracle)
Insurance Logic
As our strategies do not have a perfect hedge against IL but instead apply an approach which is akin to statistical arbitrage, extremely high volatility can lead to minor drawdowns for users. In order to help protect against this in addition to protecting against any interruptions to our off-chain infrastructure we have built in some insurance logic to our strategies. This logic essentially builds up some reserves from the gross yield at each harvest to cover up to 0.5% losses in the strategy, if there is a period where the strategy has a minor drawdown these reserves will be used to cover these losses. Note the 0.5% number was chosen based on looking at historical data of our strategies in addition to backtesting & simulations to understand how large drawdowns could get in the events of very large price movements together with some interruptions to our off-chain infrastructure.
Third Party Protocols
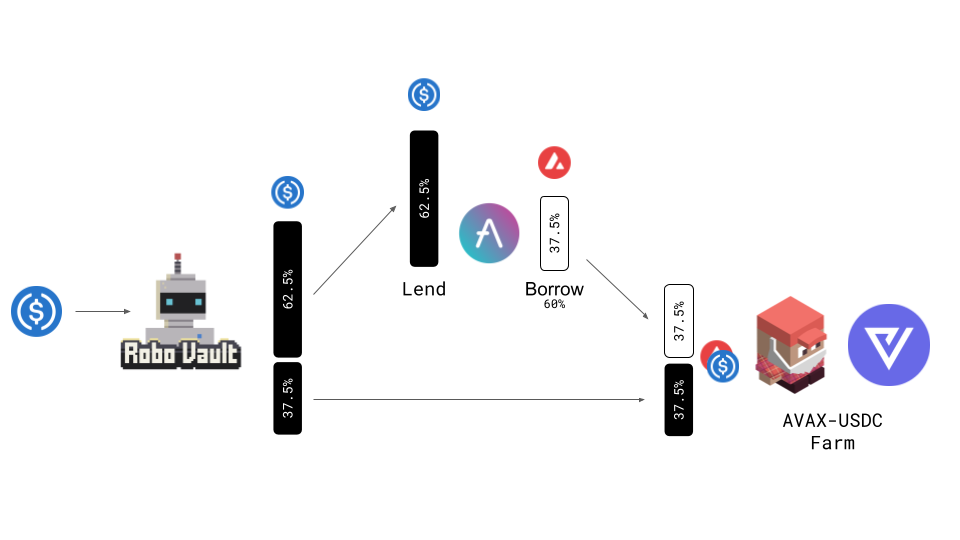
As our delta neutral strategies are built on top of other protocols including lending protocols & AMM’s we’re also extremely cautious with which protocols we build on top of. As described above SCREAM which at the time was the leading lending protocol incurred bad debt due to some errors. This shows that security is not just limited to safe smart contract code but also requires developers to be extremely cautious in how they update their code. Typically our process for vetting other protocols that are utilised in our strategies involves us checking if their code is audited, what is their track record in terms of security, can the code be updated & if it can, how is it updated (to minimise risks of future updates breaking things). For example primarily utilising AAVE for lending & borrowing within our Core Strategy who have a very strong record of strong security practices with ongoing risk management practices.
Audits + Reviews
We have worked with a number of external parties to provide external reviews of our strategies including the Byte Masons Team, Strategists that have developed strategies for Yearn. The Yearn V2 architecture we inherit has also been heavily audited and reviewed. While we’ve also completed audits on our strategy code to ensure the mechanics we use adequately protect against typical attacks & will be looking to have additional audits going forward.
Multi-Sig Controls
Our vaults are all controlled by multi sig addresses, signers include RoboVaults co-founders safetyBot & smoothBot. All signers utilise hardware wallets to ensure these addresses don’t have a risk of being compromised by malware.
Additionally safetyBot has given public speeches at FantomDeveloper conference & smoothBot will be presenting at the ChainLink conference so our identities are known by key parties within the DeFi community.
Security Training : Our lead developer Smoothbot has also completed a fellowship through Yearns yAcademy program auditing a number of contracts and gaining mentorship from various leaders in the security space
This is a high level look into the main things we’ve implemented to ensure users funds can safely be managed by our strategies. If you’ve got any questions feel free to reach out to us
Links


